Q-in-Q Tunneling is to allow service providers or hosting provider or data center, 4096 VLAN inside of each one of 4096 VLAN. This is really useful and easy to implement. Before going to the configuration part, let’s discuss the benefits of q-in-q tunnel.
Service providers often meet the requirement for specific VLAN IDs and the number of VLANs to be supported from the customer end. Those VLAN IDs might overlap and they also need to segregate from other customers. Q-in-Q helps to solve this problem.
It provides point-to-point or point-to-multipoint L2 tunnel.
When q-in-q will be configured, there will no new configuration from the service provider end. Customer need to configure on their end only for future changes. So, data connectivity will look like dark fiber to the customers.
Q-in-Q Tunneling configuration in Cisco Catalyst
Configuration of Q-in-Q tunnelling in Cisco is very simple. First let’s configure ISP inside links. We need to make sure, our mtu is enough to add extra tag for Q-in-Q tunnel.
We will follow below diagram for our LAB. So, let’s get started.
Diagram
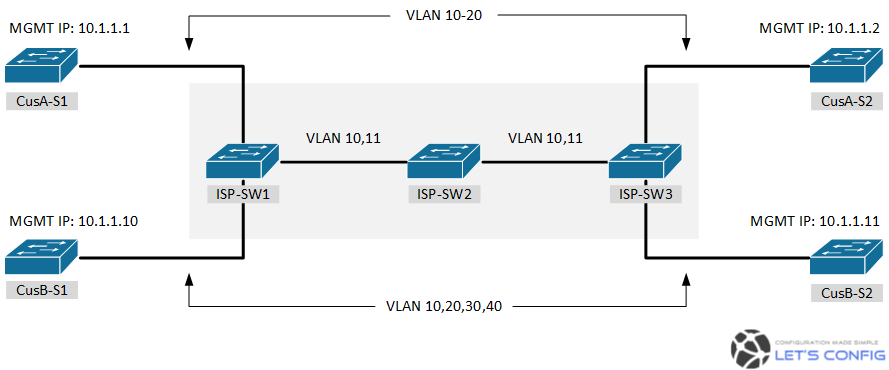
Our VLAN mapping from ISP end is below-
- CusA – VLAN 10
- CusB – VLAN 11
VLAN mapping from Customer end is below-
- CusA – VLAN 10,11,12,13,14,15,16,17,18,19,20
- CusB – VLAN 10,20,30,40
ISP-SW1 configure terminal vlan 10,11 interface GigabitEthernet0/2 description ***Connected to ISP-SW2*** switchport trunk encapsulation dot1q switchport mode trunk switchport trunk allowed vlan 10,11 mtu 1504
ISP-SW2 configure terminal vlan 10,11 interface GigabitEthernet0/2 description ***Connected to ISP-SW1*** switchport trunk encapsulation dot1q switchport mode trunk switchport trunk allowed vlan 10,11 mtu 1504 interface GigabitEthernet0/3 description ***Connected to ISP-SW3*** switchport trunk encapsulation dot1q switchport mode trunk switchport trunk allowed vlan 10,11 mtu 1504
ISP-SW3 configure terminal vlan 10,11 interface GigabitEthernet0/3 description ***Connected to ISP-SW2*** switchport trunk encapsulation dot1q switchport mode trunk switchport trunk allowed vlan 10,11 mtu 1504
Now, we will configure customer facing interfaces. Here we will enable 802.1Q tag by using “switchport mode dot1q-tunnel” command. Below we are configuring access vlan 10 for CusA and vlan 11 for CusB.
ISP-SW1 interface GigabitEthernet0/0 description ***Connected to CusA-S1*** switchport mode dot1q-tunnel switchport access vlan 10 interface GigabitEthernet0/1 description ***Connected to CusB-S1*** switchport mode dot1q-tunnel switchport access vlan 11
From ISP-SW3, we will do the similar configuration for Customer’s 2nd site (CusA-S2 and CusB-S2).
ISP-SW3 interface GigabitEthernet0/0 description ***Connected to CusA-S2*** switchport mode dot1q-tunnel switchport access vlan 10 interface GigabitEthernet0/1 description ***Connected to CusB-S2*** switchport mode dot1q-tunnel switchport access vlan 11
So, we have done with ISP end configuration. Now, we will configure customer end. It’s plain VLAN configuration and customer have full control to forward VLAN through this tunnel.
Below are the configuration of Customer A (CusA).
CusA-S1 configure terminal vlan 10-20 interface GigabitEthernet0/0 description ***Connected to ISP-SW1*** switchport trunk encapsulation dot1q switchport mode trunk switchport trunk allowed vlan 10-20 interface vlan 10 description ***MGMT VLAN*** ip add 10.1.1.1 255.255.255.0 CusA-S2 configure terminal vlan 10-20 interface GigabitEthernet0/0 description ***Connected to ISP-SW3*** switchport trunk encapsulation dot1q switchport mode trunk switchport trunk allowed vlan 10-20 interface vlan 10 description ***MGMT VLAN*** ip add 10.1.1.2 255.255.255.0
In next section, we will configure site for Customer B (CusB). To make a point, we have configured VLAN 10 in Customer B network as well along with 10.1.1.0/24 IP for MGMT just like below.
CusB-S1 configure terminal vlan 10,20,30,40 interface GigabitEthernet0/0 description ***Connected to ISP-SW1*** switchport trunk encapsulation dot1q switchport mode trunk switchport trunk allowed vlan 10,20,30,40 interface vlan 10 description ***MGMT VLAN*** ip add 10.1.1.10 255.255.255.0 CusB-S2 configure terminal vlan 10,20,30,40 interface GigabitEthernet0/0 description ***Connected to ISP-SW3*** switchport trunk encapsulation dot1q switchport mode trunk switchport trunk allowed vlan 10,20,30,40 interface vlan 10 description ***MGMT VLAN*** ip add 10.1.1.20 255.255.255.0
Useful commands:
Below are few useful command to add in Q-in-Q tunneling.
l2protocol-tunnel cdp l2protocol-tunnel stp l2protocol-tunnel vtp
Verification
Very first command will be show dot1q-tunnel from ISP edge switch.
ISP-SW1#show dot1q-tunnel dot1q-tunnel mode LAN Port(s) ----------------------------- Gi0/0 Gi0/1
It’s clearly showing we have Q-in-Q tunnel configuration in Gi0/0 and Gi0/1 interface.
Now, if our configuration is OK, then we will be able to see from CusA-S1 to CusA-S2 as a connected next-hop.
CusA-S1#show cdp neighbors
Capability Codes: R - Router, T - Trans Bridge, B - Source Route Bridge
S - Switch, H - Host, I - IGMP, r - Repeater, P - Phone,
D - Remote, C - CVTA, M - Two-port Mac Relay
Device ID Local Intrfce Holdtme Capability Platform Port ID
CusA-S2 Gig 0/0 169 R S I Gig 0/0
Total cdp entries displayed : 1Same goes for CusB-S1 to CusB-S2.
CusB-S1#show cdp neighbors
Capability Codes: R - Router, T - Trans Bridge, B - Source Route Bridge
S - Switch, H - Host, I - IGMP, r - Repeater, P - Phone,
D - Remote, C - CVTA, M - Two-port Mac Relay
Device ID Local Intrfce Holdtme Capability Platform Port ID
ISP-SW1 Gig 0/1 156 R S I Gig 0/1
Total cdp entries displayed : 1We will be able to ping Site-2 from Site-1 for Customer A but will not be able to ping to CusB-S1 and CusB-S2 due to they are in different tunnel.
CusA-S1#ping 1.1.1.2 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 1.1.1.2, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 19/40/76 ms CusA-S1# CusA-S1# CusA-S1#ping 1.1.1.10 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 1.1.1.10, timeout is 2 seconds: ..... Success rate is 0 percent (0/5) CusA-S1#
If you enjoyed. For more information, you can use cisco.com configuration guide as reference.


Great article
Seem there is no special configuration needed on the customer switches, you can just connect the CusA-S1 and CusA-S2 directly with physical cable and it will work. The QinQ part is transparent to the customer?
Also wouldn’t CDP for CustB-S1 show CustB-S2 as next hop, rather than ISP-SW1?
If there is CustA-S3 connected to ISP-SW3, then CDP for CustA-SW1 would see both of them on local port Gig 0/0? Would be tell tale sign some sort of tunnelling is going on then….
Good explanations, Thanks!
You are welcome..
Long story short, trying to test this and mostly wondering what the MAC tables would look like but can’t find a simulator/emulator that is known to have QnQ functions. Will MACs from the Customer’s inner VLANs (10-20, and 10/20/30/0) be seen on the ISP switches in VLANs 10/11’s MAC tables?
I’m guessing that since the customer MACs would be part of the inner VLANs that the ISP switches will NOT see those MACs in the outer VLANs when going through the ISP network. Can you confirm?
You can use EVE-NG or GNS3 for the lab. Both will work.
Hello Rajib,
Thanks for this very clear post. It was exactly whas i was looking for.
I think there is a typo in ISP-SW3 configuration : in my understanding, Gi 0/0 should be plugged in VLAN 10.
Hi Philippe, Yes, you are correct. It was my typing mistake. I done the correction accordingly.
Thanks.