LDAP authentication is a feature that helps to authenticate end users to access services and applications. We also can define policies based on user and/or user groups by connecting LDAP on Palo Alto. In this lesson, we will learn to configure LDAP Authentication on Palo Alto Firewall.
Configuration of LDAP Authentication
Server Profiles:
First of all, we will create Server Profiles for LDAP. For that, we need to go Device >> Server Profiles and then need to click on Add to add the profile.
Our LDAP profile name is Our-LDAP and its ip is 192.168.1.110. We are using administrator account (username) for this, however it is recommended to use a separate AD account only for this purpose.
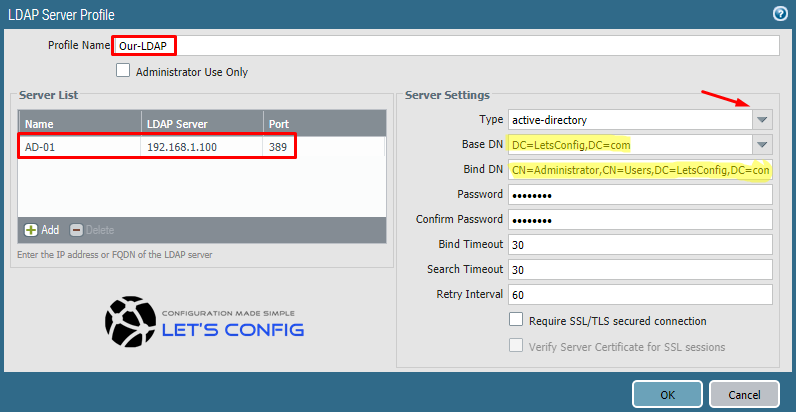
To find DC and CN for a username, you can run below command on your AD Server. Replace administrator with your username.
PS C:\Users\Prianka> dsquery user -name administrator "CN=Administrator,CN=Users,DC=LetsConfig,DC=com"
Authentication Profile:
In this section, we will go to Device >> Authentication Profile and then click on Add. Now, you need to add profile name. We named it as OUR-LDAP-AUTH, select type as LDAP from drop-down menu. Now, for Server Profile option, select newly created Server Profile. In my LAB, it is Our-LDAP (you can use drop-down menu).
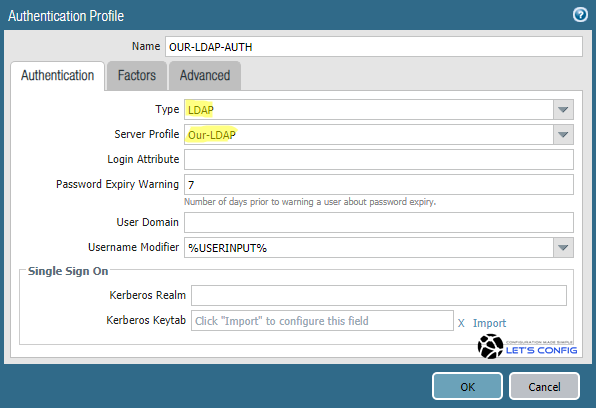
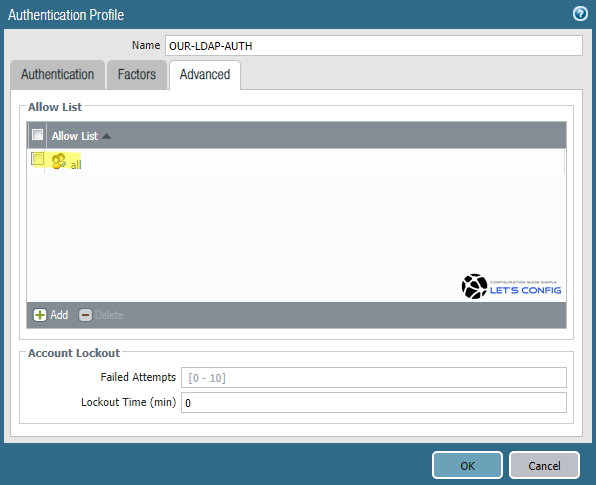
Now go to Advanced option, click Add on Allow List section and select all. And finally, click OK to add the profile.
Use of LDAP Authentication
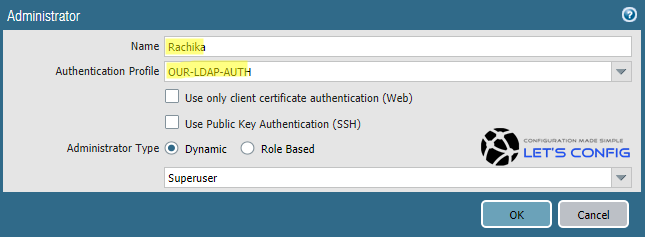
We can assign our newly created Authentication profile to provide Administrative access on Palo Alto GUI and CLI. To do this, we need to go Device >> Administrators and then click Add to add a username.
I am providing access to username Rachika (AD User) as a Superuser. So, name will be Rachika, Authentication Profile will be OUR-LDAP-AUTH and Supersuer from drop-down menu as a user type.
Now, we need to commit our changes.
Verification:
Option 1:
Just try to SSH or login to GUI using AD username Rachika and it’s AD Password.
ssh 10.1.1.34 login as: Rachika Keyboard-interactive authentication prompts from server: | Password: End of keyboard-interactive prompts from server Last login: Tue Mar 3 02:30:10 2020 from 10.1.1.1 Number of failed attempts since last successful login: 0 Rachika@PA-NGFW>
Option 2:
To verify LDAP, you can use below command-
admin@PA-NGFW> test authentication authentication-profile OUR-LDAP-AUTH username Rachika password Enter password : Target vsys is not specified, user "Rachika" is assumed to be configured with a shared auth profile. Do allow list check before sending out authentication request... name "Rachika" is in group "all" Authentication to LDAP server at 192.168.1.100 for user "Rachika" Egress: 10.1.1.34 Type of authentication: plaintext Starting LDAP connection... Succeeded to create a session with LDAP server DN sent to LDAP server: CN=Rachika Das,CN=Users,DC=LetsConfig,DC=com User expires in days: never Authentication succeeded for user "Rachika"

