Earlier we discussed, how to configure policy-based IPSec vpn on Juniper SRX and now we are going to discuss about route based IPSec. So, in this lesson, I will be discussing, how to configure Site-to-Site Route based IPSec VPN on Juniper SRX.
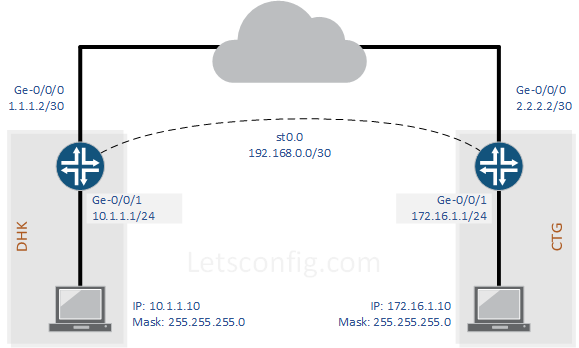
VPN Details:
| Description | DHK SRX | CTG SRX |
| VPN Gateway IP (WAN) | 1.1.1.2 | 2.2.2.2 |
| LAN IP | 10.1.1.0/24 | 172.16.1.0/24 |
| Tunnel Interface IP (St0.0) | 192.168.0.1/30 | 192.168.0.2/30 |
VPN NegotiationParameters:
| Phase 1 | |
| Authentication Method | Pre-Shared Key |
| Authentication-algorithm | sha-256 |
| Diffie-Hellman Group | Group 5 |
| Encryption Algorithm | 3des-cbc |
| Lifetime (for renegotiation SEC) | 86400 |
| Main or Aggressive Mode | Main |
| Pre Shared Key | letsconfig |
| Phase 2 | |
| Encapsulation (ESP or AH) | ESP |
| Encryption Algorithm | 3des-cbc |
| Authentication Algorithm | hmac-sha1-96 |
| Perfect Forward Secrecy | No PFS |
| Lifetime (for renegotiation) | 28800 |
Configuration:
Let’s assume, everything is configured except the IPSec VPN. Which means, we have full reachability from DHK srx to CTG srx as per our LAB diagram.
So, let’s verify the ping from DHK end to CTG end IP.
root@DHK> ping 2.2.2.2 PING 2.2.2.2 (2.2.2.2): 56 data bytes 64 bytes from 2.2.2.2: icmp_seq=0 ttl=63 time=11.684 ms 64 bytes from 2.2.2.2: icmp_seq=1 ttl=63 time=10.274 ms 64 bytes from 2.2.2.2: icmp_seq=2 ttl=63 time=10.190 ms 64 bytes from 2.2.2.2: icmp_seq=3 ttl=63 time=10.640 ms ^C --- 2.2.2.2 ping statistics --- 4 packets transmitted, 4 packets received, 0% packet loss round-trip min/avg/max/stddev = 10.190/10.697/11.684/0.594 ms root@DHK>
Ping result shows, a full reachability to IPSec peer IP. Now, we need to verify system-service ike are allowed on the external interface or not?
DHK: root@DHK# run show config | match UNTRUST | match system-services | display set set security zones security-zone UNTRUST host-inbound-traffic system-services ike CTG: root@CTG# run show config | match UNTRUST | match system-services | display set set security zones security-zone UNTRUST host-inbound-traffic system-services ike
Now, let’s configure st0.0 (tunnel interface) for both SRX end.
DHK: root@DHK# set interfaces st0.0 family inet address 192.168.0.1/30 CTG: root@CTG# set interfaces st0.0 family inet address 192.168.0.2/30
Now, we need to define zone for st0.0 interface. In our lab, we named it VPN and for simplicity, we are allowing all protocol and services on this VPN zone.
VPN zone configuration on DHK & CTG srx: set security zones security-zone VPN host-inbound-traffic system-services all set security zones security-zone VPN host-inbound-traffic protocols all set security zones security-zone VPN interfaces st0.0
Next, we need to configure proper policies for VPN zone. It’s our LAB, that’s why we have default policy which allow everything. You need to make the policy as per your requirements.
DHK: root@DHK# run show configuration security policies | display set set security policies default-policy permit-all CTG: root@CTG# run show configuration security policies | display set set security policies default-policy permit-all
In the next step, we will configure IKE proposal and IKE policy for both SRX.
Proposal for DHK & CTG SRX: set security ike proposal OUR-IKE-PROPOSAL authentication-method pre-shared-keys set security ike proposal OUR-IKE-PROPOSAL dh-group group5 set security ike proposal OUR-IKE-PROPOSAL authentication-algorithm sha-256 set security ike proposal OUR-IKE-PROPOSAL encryption-algorithm 3des-cbc set security ike proposal OUR-IKE-PROPOSAL lifetime-seconds 86400 Policy for DHK & CTG SRX: set security ike policy OUR-IKE-POLICY mode main set security ike policy OUR-IKE-POLICY proposals OUR-IKE-PROPOSAL set security ike policy OUR-IKE-POLICY pre-shared-key ascii-text letsconfig
In IKE gateway, we need to bind policy and gateway with external interface. Below are the commands-
DHK: set security ike gateway OUR-IKE-GATEWAY ike-policy OUR-IKE-POLICY set security ike gateway OUR-IKE-GATEWAY address 2.2.2.2 set security ike gateway OUR-IKE-GATEWAY external-interface ge-0/0/0.0 CTG: set security ike gateway OUR-IKE-GATEWAY ike-policy OUR-IKE-POLICY set security ike gateway OUR-IKE-GATEWAY address 1.1.1.2 set security ike gateway OUR-IKE-GATEWAY external-interface ge-0/0/0.0
Configuring DPD, is really good practice, but not mandatory. If you want to configure DPD then, below are the sample commands-
set security ike gateway OUR-IKE-GATEWAY dead-peer-detection interval 20 set security ike gateway OUR-IKE-GATEWAY dead-peer-detection threshold 5
Now, let’s configure IPSec proposal an IPSec policy for both DHK and CTG SRX.
Proposal for DHK & CTG: set security ipsec proposal OUR-IPSEC-PROPOSAL protocol esp set security ipsec proposal OUR-IPSEC-PROPOSAL authentication-algorithm hmac-sha1-96 set security ipsec proposal OUR-IPSEC-PROPOSAL encryption-algorithm 3des-cbc set security ipsec proposal OUR-IPSEC-PROPOSAL lifetime-seconds 28800 Policy for DHK & CTG: set security ipsec policy OUR-IPSEC-POLICY proposals OUR-IPSEC-PROPOSAL
After completing IPsec proposal and policy, we need to configure IPSec VPN. Below are the configuration of VPN for both DHK & CTG srx.
set security ipsec vpn OUR-VPN bind-interface st0.0 set security ipsec vpn OUR-VPN ike gateway OUR-IKE-GATEWAY set security ipsec vpn OUR-VPN ike ipsec-policy OUR-IPSEC-POLICY set security ipsec vpn OUR-VPN establish-tunnels immediately
Finally, we need to configure a route between 10.1.1.0/24 and 172.16.1.0/24. We are configuring a static route and next-hop will be st0.0 interface.
DHK: set routing-options static route 17.16.1.0/24 next-hop st0.0 CTG: set routing-options static route 10.1.1.0/24 next-hop st0.0
Verification:
First of all, you need to initiate traffic from one end to another. Otherwise, you might find IKE & IPSec security-associations down. In our case, after pining from 10.1.1.10 to 172.16.1.10 we have the reachability.
C:\>ping 172.16.1.10
Pinging 172.16.1.10 with 32 bytes of data:
Reply from 172.16.1.10: bytes=32 time=14ms TTL=126
Reply from 172.16.1.10: bytes=32 time=12ms TTL=126
Reply from 172.16.1.10: bytes=32 time=12ms TTL=126
Reply from 172.16.1.10: bytes=32 time=14ms TTL=126
Ping statistics for 172.16.1.10:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 12ms, Maximum = 14ms, Average = 13msBelow are two commands to verify phase-1 and phase-2 status.
show security ike security-associations show security ipsec security-associations
Phase-1: root@DHK# run show security ike security-associations Index State Initiator cookie Responder cookie Mode Remote Address 4585457 UP 5410b5bbf9ead488 06e72f5214e7aa5a Main 2.2.2.2 Phase-2: root@DHK# run show security ipsec security-associations Total active tunnels: 1 ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway <131073 ESP:3des/sha1 a4ca610 28518/unlim - root 500 2.2.2.2 >131073 ESP:3des/sha1 d7d57d73 28518/unlim - root 500 2.2.2.2
So, it’s working 🙂
Juniper provides a fantastic tool to generate Site-to-Site VPN Configuration for SRX & J Series devices. Please have a look – https://www.juniper.net/support/tools/vpnconfig/


Great tutorial, I enjoyed it very much in my lab, thank you!
You’re welcome! I’m glad the tutorial was helpful.
Dear Mr. RAJIB,
Thank you for your guide,
I have based on your configuration platform for IPSec VPN, set up 3 brands working well,
Best regards and thanks,
Quoc Mai,
Hi Quoc Mai, I am glad to know, my tutorial helped you.
Hi,
i have a main office and three branches, please provide the same configuration as ipsec for this system.
Thank you,
You can use this confirmation as reference to build you scripts. If you need my direct help, do contact me through https://www.letsconfig.com/contact/.