Palo Alto Wildfire service is a cloud based analysis techniques to detect malware and then generate signature to protect from them. For simplicity you can says, it’s turns unknown malware into known malware. Today, in this lesson we will learn how to configure wildfire in Palo Alto firewall.
How wildfire works?
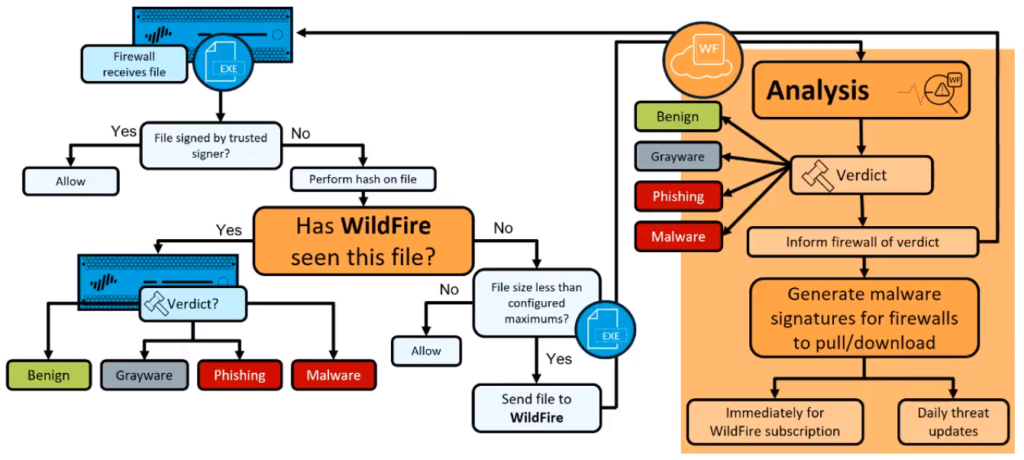
First, the firewall receives a file. Then the firewall checks to see, if the file has been signed by a trusted digital signature. If it has, then the file would be allowed. If it has not then the firewall will take a hash of the file. Then it will check against wildfire, to see if that hash has been seen before.
If that hash has been seen before, then there will be a verdict associated, benign, grayware/phishing or malware verdicts. However, if wildfire has not seen this file before, then the fire will check to see, if the file size is smaller than the configured maximum thresholds.
If the file is too large then the firewall has no option but to allow the file. However, if the file is not too large, then it can be submitted up to wildfire for analysis. Once the analysis is complete, a verdict will be generated based on the characteristics and behavior of the file and that verdict would be again benign, grayware, phishing or malware.
After that then wildfire will inform the submitting firewall of this verdict and this will appear within the wildfire submissions log. After which, wildfire will generate malware signatures and make them available for firewalls to download. If your firewall has a valid wildfire subscription, you can immediately download the signature, once it’s placed on the update server, after about a five minute period. If your firewall does not have a wildfire subscription you still benefit from the submission of this file during the next days antivirus update.
Palo Alto Wildfire Deployment options
- Global Cloud: WildFire Public cloud
- Private Cloud: WildFire Appliance WF-500
- Hybrid Cloud: Combination of Public cloud and appliance
How to configure Palo Alto wildfire?
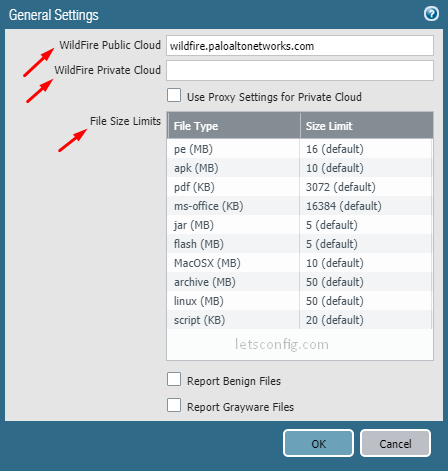
Go to Device >> Setup >> WildFire and click General Settings.
You will find URL for public cloud. You can choose your desire public cloud if you are using global wildfire. If you using appliance then add ip address of your WildFire Private Cloud. You also can change default file size here.
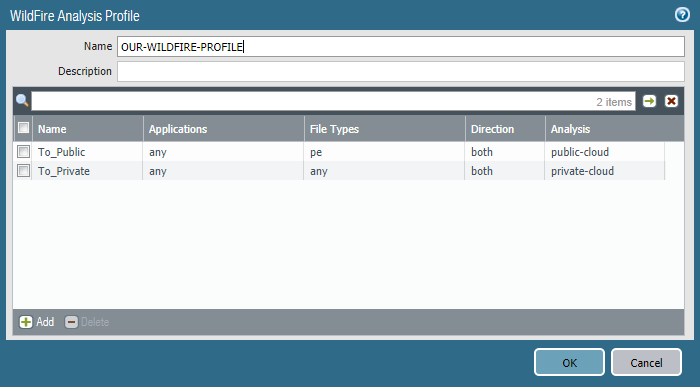
Now, go to Objects >> Security Profiles >> WildFire Analysis and click Add. You can define file types and destination cloud (private/public).
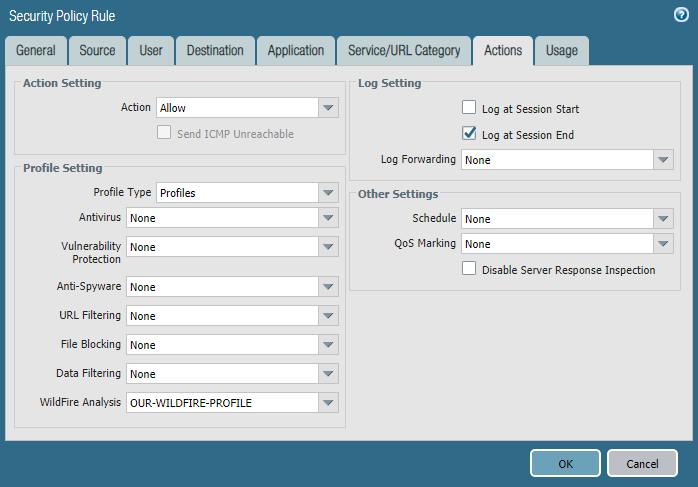
Finally, go to Policies >> Security and click on your desire policy, mostly it will be access-to-internet policy. Go to Actions of the policy and select Profiles in profile type. Choose your newly create Wildfire analysis profile. In my case it is OUR-WILDFIRE-PROFILE.
Test a sample Malware File:
If you have SSL decryption enabled on the firewall, use one of the following URLs:
- PE—https://wildfire.paloaltonetworks.com/publicapi/test/pe
- APK—https://wildfire.paloaltonetworks.com/publicapi/test/apk
- MacOSX—https://wildfire.paloaltonetworks.com/publicapi/test/macos
- ELF—wildfire.paloaltonetworks.com/publicapi/test/elf
If you do not have SSL decryption enabled on the firewall, use one of the following URLs instead:
- PE—http://wildfire.paloaltonetworks.com/publicapi/test/pe
- APK—http://wildfire.paloaltonetworks.com/publicapi/test/apk
- MacOSX—http://wildfire.paloaltonetworks.com/publicapi/test/macos
- ELF—wildfire.paloaltonetworks.com/publicapi/test/elf
Verification:
To test the connect between firewall and wildfire cloud, run test wildfire registration command.
admin@PA-FW-01> test wildfire registration
This test may take a few minutes to finish. Do you want to continue? (y or n)
Test wildfire Public Cloud
Testing cloud server wildfire.paloaltonetworks.com ...
wildfire registration: successful
download server list: successful
select the best server: panos.wildfire.paloaltonetworks.com
Test wildfire Private Cloud
Cloud server is empty
admin@PA-FW-01> You also can run –
show wildfire status channel public show wildfire status channel private
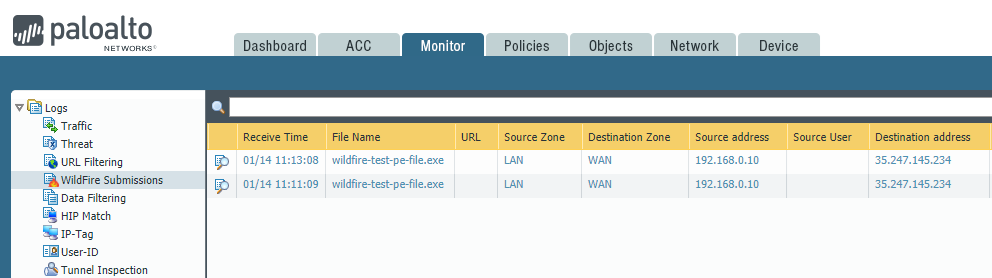
To check submission, go to Monitor >> Logs >> WildFire Submission.